Overview
Introduction
M&NTIS Platform is an adversary simulation and systems simulation solution information, based on a Cyber Range technology.
M&NTIS Platform aims to challenge investments in cybersecurity (products, service providers, internal teams and architecture designs), making it possible to measure the level of effectiveness of the solutions and identify areas with a low level of maturity in cybersecurity, and therefore at risk.
M&NTIS Platform also helps demonstrate regulatory compliance, on subjects relating to effectiveness in defense (PDIS and PRIS repositories of ANSSI) and concerning the implementation of crisis management exercises (NIS2 directive and DORA regulation).
As illustrated in the following diagram, M&NTIS Platform is based on two components:
- A Cyber Range technology, making it possible to simulate information systems (IS).
- An adversary emulation technology, allowing realistic offensive scenarios to be played on the simulated IS.
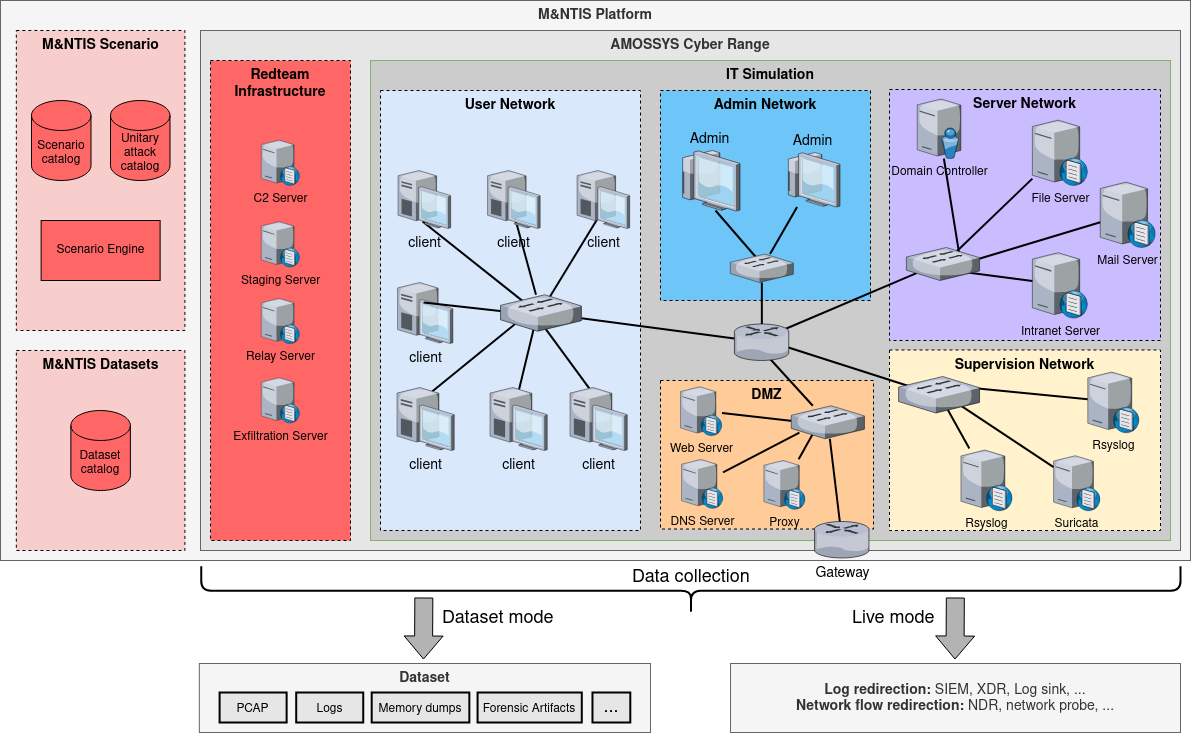
The Cyber Range engine allows IT architectures to be simulated, relying on virtual machines and networked containers. This engine allows the interconnection of the simulated IS with physical equipment, local subnetworks as well as the Internet.
Interaction with the simulated environment
M&NTIS Platform users can interact with the simulated environment to, for example, perform these operations:
- Extend the simulated information system (provisioning).
- Inspect the impact of the attack steps (system and business impacts, traces and artifacts left behind, etc.).
- Carry out targeted investigations on workstations and servers in real time.
- Test and implement countermeasures on the simulated IS.
By following the principle of Infrastructure as Code, the SI simulation engine allows you to take as input a formalization of the IS architecture and to instantiate the simulated IT in a reproducible manner. Therefore, the work of developing the IS within the Cyber Range is very simplified.
Furthermore, M&NTIS Platform facilitates and encourages the use of automated provisioning of resources and services within virtual machines. A catalog of integrations in defense (set of Ansible playbooks provided with the platform) is notably available natively, thus facilitating the use of M&NTIS as a complete attack - defense platform.
Adversary Emulation Engine
The adversary emulation engine allows you to implement complex attack scenarios by implementing the concept of cyber kill chain, and by relying on a catalog of attacks classified according to the MITRE ATT&CK repository.
This emulation engine adversary executes scenarios while ensuring consistency in the sequence of attack actions (i.e. the results of an attack can be used as input to a next attack).
The execution of attacks is automated, and relies on the instrumentation of intrusive testing tools, thus realistically reproducing attackers’ operating methods. At the exit, M&NTIS Platform is able to produce the explainability of the attack scenarios played on the simulated IS environment (i.e. visualization of the attack path and access to metadata structured of each attack step).
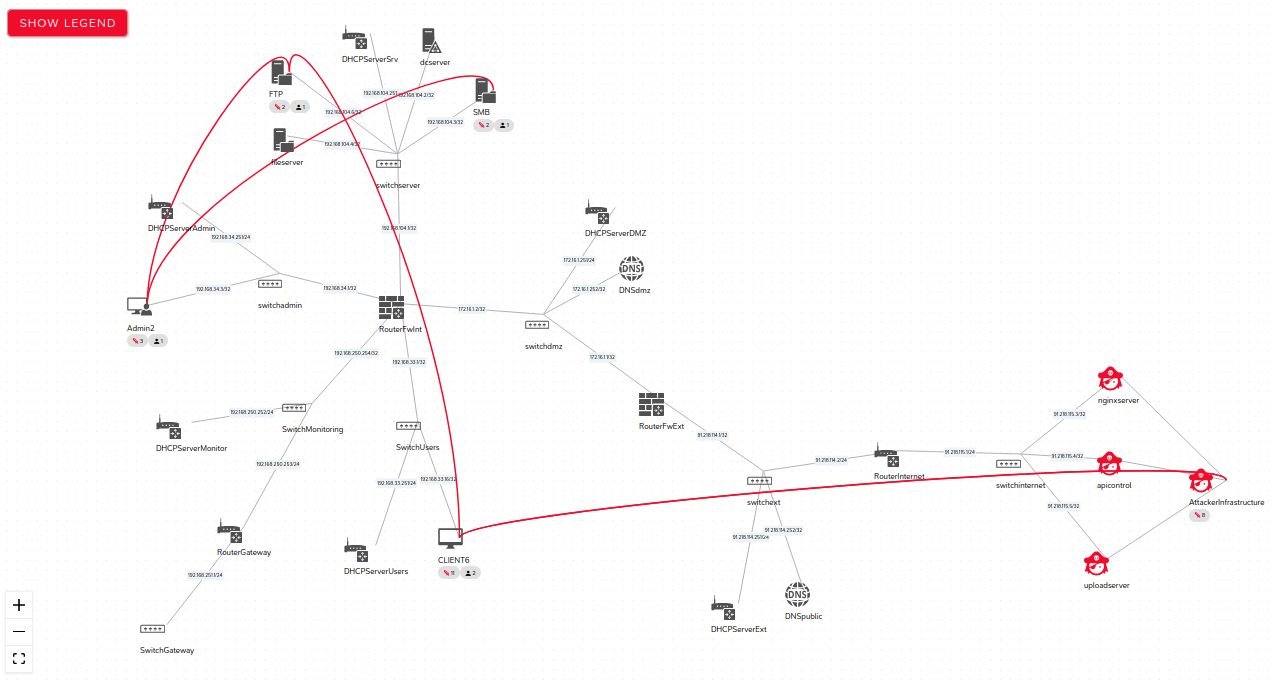
The traces produced on the simulated IS, through the legitimate activity of the IS, as well as by the attack actions can be collected within datasets. These datasets, made up of PCAP network traces, system and application logs or even memory dumps, can then be analyzed and exploited by third-party tools.
Catalogs available within M&NTIS Platform
M&NTIS Platform provides a set of catalogs so that users can quickly focus on their business needs. There are thus available:
- A catalog of IS topologies.
- A catalog of Ansible provisioning playbooks, allowing you to automate the customization of simulated IS nodes (deployment of resources, applications, AD configuration, etc.).
- A catalog of defense security product integrations (collection agents, network probes, EDR, SIEM, etc.).
- A catalog of legitimate life actions and user profiles.
- A catalog of attacks, including the MITRE ATT&CK taxonomy.
- A catalog of complete attack scenarios (killchains), based on a coherent sequence of attacks which can integrate life actions (user phishing for example).
These public catalogs can be extended and completed for the specific needs of a customer (notion of private catalogs).
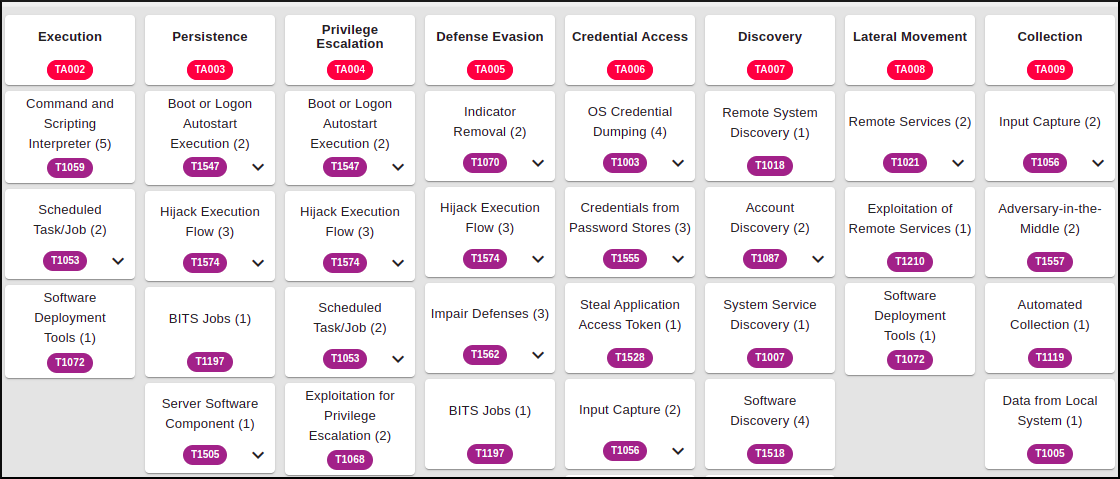
The catalog of attacks is represented according to the MITRE ATT&CK matrix:
How M&NTIS Platform works
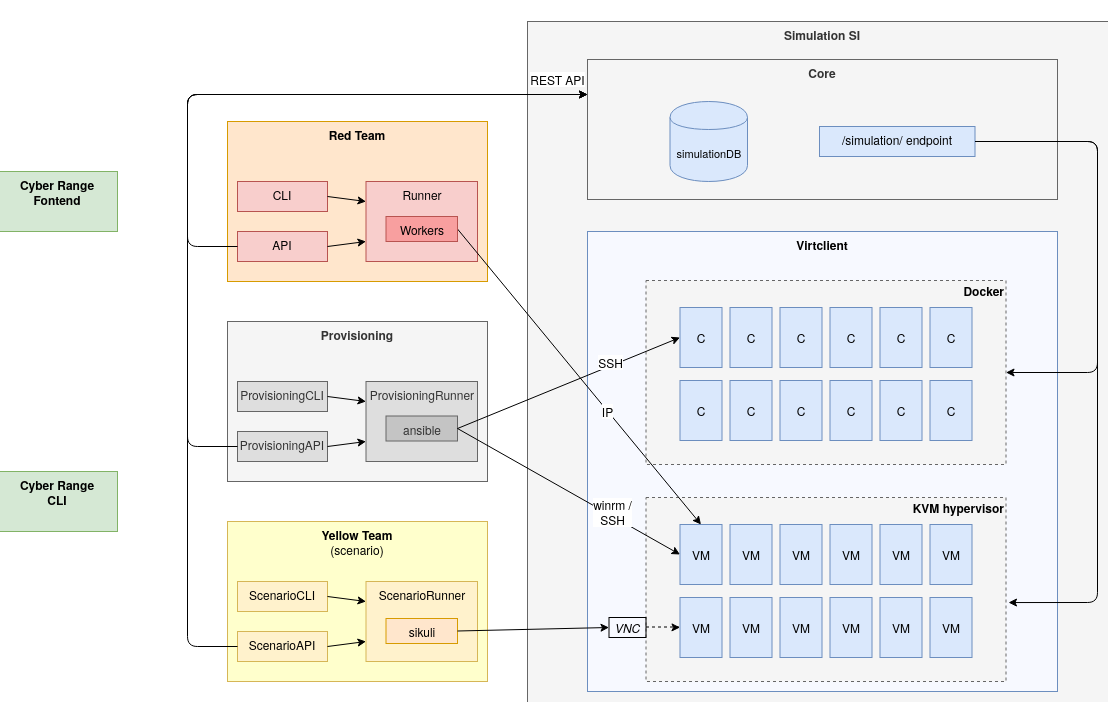
As shown in the figure below, from a functional point of view, several components are responsible for ensuring the production and execution of static and dynamic life content within the M&NTIS Platform Cyber Range. These components interconnect in the following manner on the SI simulation environment:
- Red Team Component: the red team component logs in IP on the targeted VMs, through an attack infrastructure generated dynamically for the needs of the attack scenario.
- Provisioning Component: the provisioning component connects using winrm to the Windows machines and SSH to th Linux machines in order to run Ansible playbooks.
- User activity Component (Yellow Team): the user activity component works without an agent, and connects to virtual machines using remote VNC display exposed by the hypervisor.
Access to features
M&NTIS Platform and all resources can be manipulated either:
- From the M&NTIS web frontend.
- From the M&NTIS CLI.
- By REST API or Python API scripts.

