July 22, 2025
NIDS signature testing using M&NTIS
Introduction: Creating a stimuli for a new signature
By using M&NTIS Platform, a SOC detection engineering team can test its rules before they are deployed to a production system. This use case is particularly relevant for testing the detection of a new CVE exploit. As an example, a recent attack of CVSS’s score of 9.8 has been discovered against Langflow: CVE-2025-3248. The description associated is “Langflow versions prior to 1.3.0 are susceptible to code injection in the /api/v1/validate/code endpoint. A remote and unauthenticated attacker can send crafted HTTP requests to execute arbitrary code.”
The script used is https://github.com/verylazytech/CVE-2025-3248/blob/main/cve-2025-3248.py to perform the attack.
The SOC analysts can create a rule to detect this specific implementation. In this article, the Sigma rule format is used. It allows a user to convert this generic format to different SIEM rule format.
Using SIGMA signatures
After an analysis of the script used by attackers for CVE-2025-3248, the SOC emitted an experimental rule in the Sigma format. The following rule is the one the SOC team has prepared in order to test it.
title: Langflow CVE-2025-3248 Exploitation Attempt
id: 5c0b1c1f-73b9-49e6-8672-b9b0c1f5e324
status: experimental
description: >
Detects POST requests to /api/v1/validate/code
to execute Python arbitrary remote code execution CVE-2025-3248 (Langflow RCE) – technique,
used by the Flodrix botnet
author: AMOSSYS
date: 2025/07/08
tags:
- attack.t1190 # Exploit Public-Facing Application
- attack.t1059.006 # Command & Script Interpreter: Python
- cve.2025.3248
- malware.flodrix
logsource:
category: tcpdump
detection:
selection_uri:
uri_path|contains: "/api/v1/validate/code"
http_method: "POST"
selection_body:
request_body|contains:
- "exec("
- "subprocess"
level: high
Converting to Suricata rule format
The SOC team uses Suricata as network probe in their computer system. This Sigma rule needs to be converted to a compatible format for Suricata. Different tools can be found on internet in order to convert such rule to an usable Suricata format. In this article, the rule is manually converted for Suricata.
alert http any any -> any any ( msg:"WEB-APP Langflow CVE-2025-3248 RCE exploit attempt (Flodrix)"; flow:established,to_server; content:"POST"; http_method; nocase; content:"/api/v1/validate/code"; http_uri; nocase; fast_pattern; content:"exec("; http_client_body; nocase; content:"subprocess"; http_client_body; nocase; classtype:web-application-attack; reference:cve,2025-3248; sid:6003248; rev:1;)
M&NTIS Lab preparation
Launching the topology
The M&NTIS Lab used for this test relies on the pre-deployment of a Linux beacon, named linux_python_reverse_api, from the M&NTIS catalog. Basically, it installs a beacon so that the machine can receive different attack commands from the user. We use this beacon to trigger the CVE exploit.
The lab is launched using the following command:
mantis attack run linux_python_reverse_api --lab_config ~/config_suricata.yaml --scenario_profile linux
The content of the file config_suricata.yaml, which allows to automatically deploy a logstash and Suricata defensive stack, is the following:
---
config_name: "Suricata"
net_capture: true
log_collectors:
- instance_name: logstash
collector_name: logstash
collector_type: aggregator
location:
- location_type: new_node
value: logstash
- instance_name: suricata
collector_name: suricata
collector_type: probe
location:
- location_type: new_node
value: suricata
The logstash log aggregator is used to receive alerts emitted by Suricata.
The resulting topology is the following one:
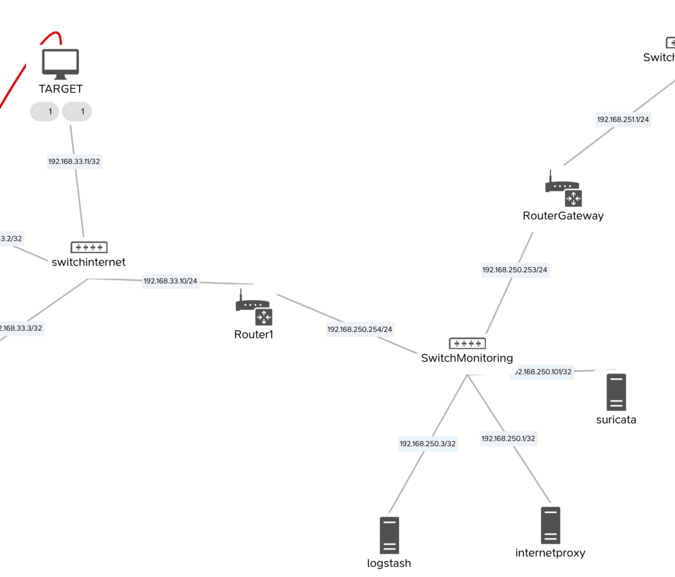
The TARGET is the node where the stimuli is going to be executed.
The Suricata node is deployed in the lab as well.
During this session, the M&NTIS Lab ID is e2f8af76-e47f-41a2-9d90-11aaea1c8038.
Configuring Suricata rules
So far, Suricata has only a few rules deployed on it.
We have to upload our new rule in order for it to be taken into account.
This is possible by deploying a publicly available ansible playbook configure-suricata.
You can follow the guide to learn how to deploy a playbook on a running M&NTIS Lab.
Exploit import in M&NTIS Lab
We use a Linux virtual machine in the lab to perform the attack. It is possible to import and execute the exploit code to this machine either by:
- using the M&NTIS relay server, which allows to manually import/export files to/from a running M&NTIS Lab,
- or by using the M&NTIS CLI to automatically trigger custom attacks on the running beacon.
Exploit import through the M&NTIS relay server
The M&NTIS relay server is accessible on the Interactive view of the M&NTIS web interface. A web page allows you to upload any file. Here, we upload the cve-2025-3248.py.
Then it is accessible from the machine at the address http://relay.mantis/webdav/uploads/cve-2025-3248.py. One can connect to the remote machine using Spice and wget the file from a terminal.
Exploit import from Internet
Another way to retrieve the script is by using the M&NTIS HTTP proxy in the lab, which allows direct access to Internet. The user can run the command http_proxy=http://192.168.250.1:3128 wget https://raw.githubusercontent.com/verylazytech/CVE-2025-3248/refs/heads/main/cve-2025-3248.py. This can be executed directly from the graphical user interface of the virtual machine (through Spice remote acces), or using the mantis CLI. In the latter case, you would get the following interactive prompt:
$ mantis lab e2f8af76-e47f-41a2-9d90-11aaea1c8038 redteam command execute
Choose one attack session in list:
[UP] 0 : 1c600ddb-ce28-4a48-bcaf-7d874eee5d73, adurand (privilege user) on TARGET (192.168.33.11)
Select attack session index: 0
Command to execute (one line): http_proxy=http://192.168.250.1:3128 wget https://raw.githubusercontent.com/verylazytech/CVE-2025-3248/refs/heads/main/cve-2025-3248.py
Command need to be executed in background, y or n ? (n by default) n
Max waiting time for command result in seconds ? (60 by default) 10
Exploit execution in M&NTIS Lab
Once the exploit has been imported to the Linux virtual machine node, it’s time to trigger it. Keep in mind that this script shall be executed in isolated environment only, such as M&NTIS Lab.
The exploit expects a targeting listening web server. In our example, we will simply use the M&NTIS HTTP proxy available in the lab as a target, even the target server does not need to be vulnerable. The proxy is accessible via http://192.168.250.1:3128. The stimuli can be executed using either the M&NTIS CLI or directly on the virtual machine (through Spice access). Using the M&NTIS CLI will look like this:
$ mantis lab e2f8af76-e47f-41a2-9d90-11aaea1c8038 redteam command execute
Choose one attack session in list:
[UP] 0 : 1c600ddb-ce28-4a48-bcaf-7d874eee5d73, adurand (privilege user) on TARGET (192.168.33.11)
Select attack session index: 0
Command to execute (one line): python3 /home/adurand/cve-2025-3248.py http://192.168.250.1:3128 whoami
Command need to be executed in background, y or n ? (n by default) n
Max waiting time for command result in seconds ? (60 by default) 10
______ _______ ____ ___ ____ ____ _________ _ _ ___
/ ___\ \ / / ____| |___ \ / _ \___ \| ___| |___ /___ \| || | ( _ )
| | \ \ / /| _| __) | | | |__) |___ \ |_ \ __) | || |_ / _ \
| |___ \ V / | |___ / __/| |_| / __/ ___) | ___) / __/|__ _| (_) |
\____| \_/ |_____| |_____|\___/_____|____/ |____/_____| |_| \___/
__ __ _ _____ _
\ \ / /__ _ __ _ _ | | __ _ _____ _ |_ _|__ ___| |__
\ \ / / _ \ '__| | | | | | / _` |_ / | | | | |/ _ \/ __| '_ \
\ V / __/ | | |_| | | |__| (_| |/ /| |_| | | | __/ (__| | | |
\_/ \___|_| \__, | |_____\__,_/___|\__, | |_|\___|\___|_| |_|
|___/ |___/
@VeryLazyTech - Medium
[*] Sending payload to http://192.168.250.1:3128/api/v1/validate/code
[*] Status Code: 404
[*] Raw Response: <!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">
[...]
[+] Command Output:
(...)
The exploit shall fail if executed on a non web vulnerable server. However, the web request is executed against the remote server, which is sufficient to test the Suricata network signature.
Validation
Network traces
The PCAP file generated during the M&NTIS Lab execution can be retrieved if necessary. Ensure the expected behavior is executed. Here, we shall have both the target uri,
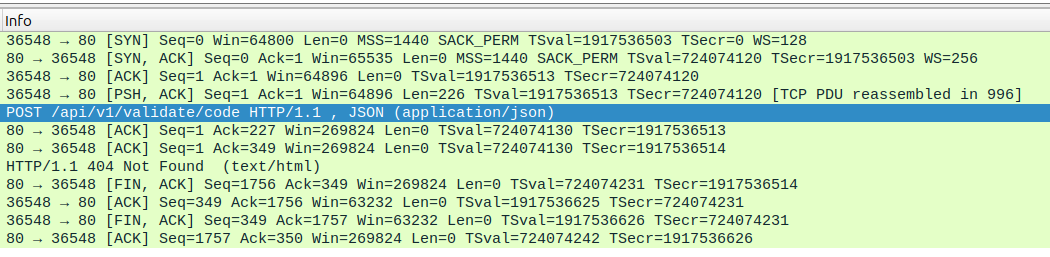
and some python commands in a post request.
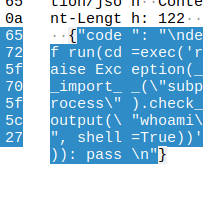
The script sucessfully executed. The user must now check if an alert was triggered.
Probe alert
If an alert is triggered by Suricata, then it is written in fast.log.
The user can access to the Suricata probe by using Spice remote access to the Suricata node.
For the example, Suricata has alerted the following:
07/08/2025-16:24:58.133142 [**] [1:6003248:1] WEB-APP Langflow CVE-2025-3248 RCE exploit attempt (Flodrix) [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 192.168.33.11:36548 -> 192.168.250.1:3128
It means the rule has successfully been triggered. The SOC analysts can further complete testing of this signature, for example by challenging it against legitimate network datasets to test for the absence of false positives.
Conclusion: Automating NIDS ruleset validation
Using M&NTIS, SOC teams can confidently validate detection rules before deployment in production environments. In this article, we illustrated how to simulate and detect an exploitation attempt of CVE-2025-3248 targeting Langflow. By crafting a Sigma rule and translating it into a Suricata-compatible format, we verified the detection capabilities through a realistic lab environment. The rule successfully triggered alerts in Suricata when the exploit script was executed, confirming its effectiveness.
This process not only strengthens the SOC’s detection posture but also ensures that security mechanisms are proactively tested against real-world threats. In addition, M&NTIS may be used for automatically and periodically testing a complete NIDS ruleset, so that a SOC team can check for non regression in terms of detection efficiency.

