Download our free dataset
This example dataset gives you an overview of what can be automatically generated by M&NTIS Platform. This dataset has been produced by executing an attack scenario based on the Zerologon vulnerability exploitation, and by playing a whole kill chain on a targeted information system. This information system runs inside a Cyber Range isolated environment, in order to provide realistic attack network and log traces. Furthermore, on each client computer, an agent-less bot plays several user behaviors. The generated dataset thus contains both legitimate and malicious activities. This dataset will be sent to you after your request, please check your spam folder if you do not receive it.
What is in our dataset?
Our dataset is a ZIP archive composed of:- A PCAP file containing the network activity captured from specific tap positions.
- An event log file for each node (computers and servers) on the network topology.
- An attack report containing metadata detailing each attack step (timestamps of actions, targeted node(s), relay node(s), attack command(s), ...).
- A user activity report for each computer node on the network topology, containing metadata detailing user behaviors (timestamps of actions, mail/internet/file activity, ...).
Zerologon attack scenario
This basic scenario is given as an example to show you the available elements in our datasets. M&NTIS platform has a much more complete catalog of attacks, and will be continuously updated with recent scenarios.
Information System architecture
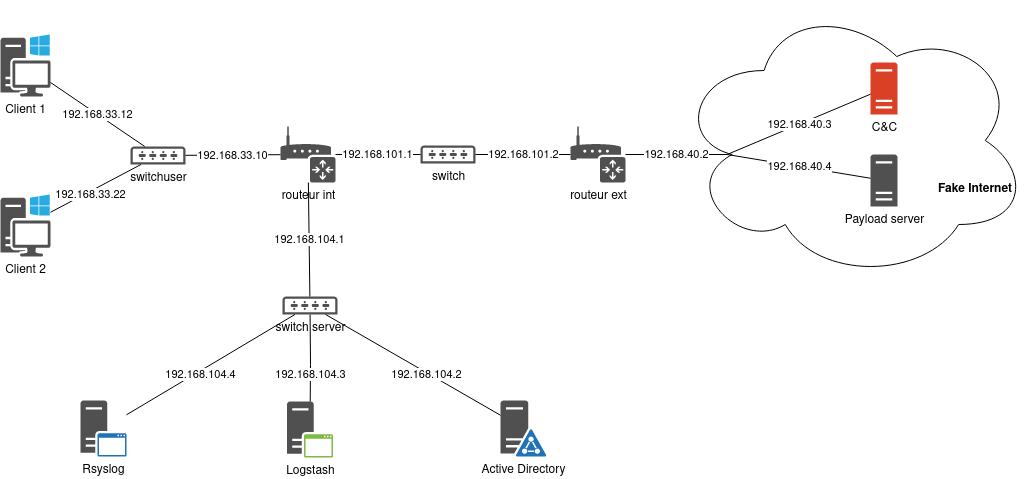
The compromission started on computer "Client 1" and finally infected the AD server.
Attack scenario content
The Zerologon scenario consists of the following steps:
- Initial compromise of the target with a RAT connected to our C&C (T1059).
- Disable Windows event logging (T1562.002).
- Disable Windows system firewall (T1562.004)
- Extract system configuration (T1592.004)
- Several scans are performed (T1046):
- discovery of the AD address,
- discovery of open ports and netbios name.
- netbios_scan
- Zerologon attack (T1210).
- Dump of the NTDS database with SMB (T1003.001).
- Winrm connections from the client computer to the AD server thanks to the extracted NTLM hash (T1021.006).

