Configure defense
Description
Agents
Those are software installed on a machine. They aim at sending logs to a log collector
Endpoint Detection and Response (EDR)
Such software are installed on a machine. In addition to sending logs to a log collector, they can generate alerts and intervene in real time during the simulation. By default in M&NTIS, they only alert on events and they do not block an attack.
Security Information and Event Management (SIEM) and XDR
A SIEM aims at collecting logs from different sources. It can generate alerts based on such logs. In some cases, they directly receive alerts and expose them to the user.
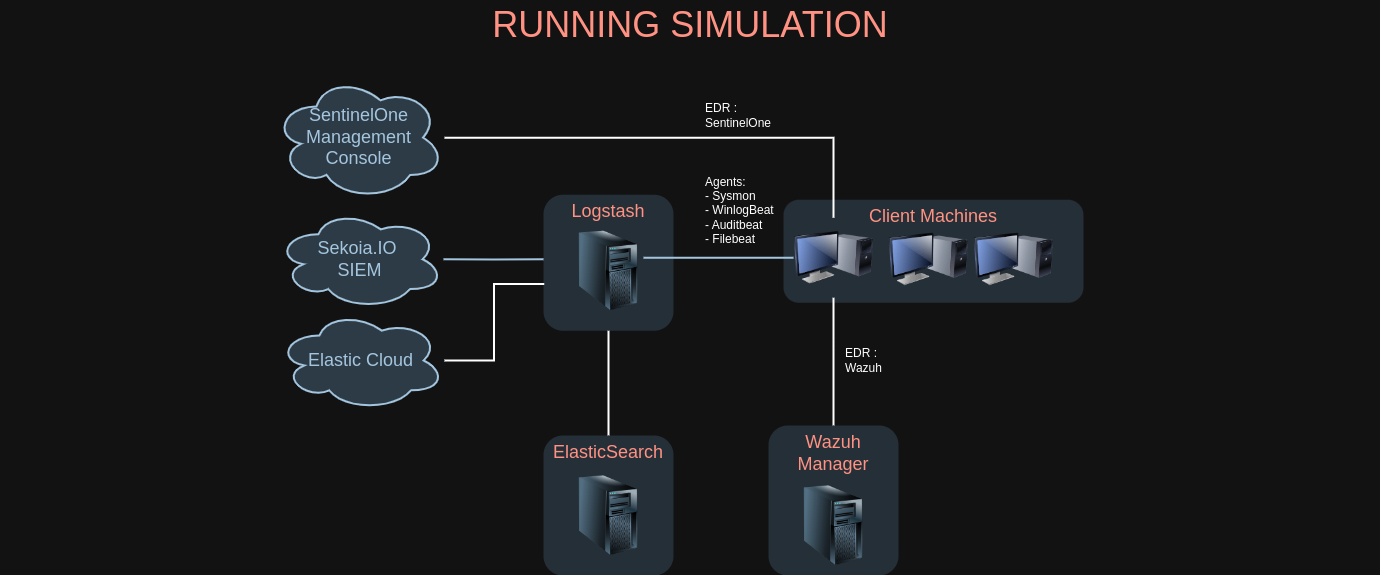
General schema
The general architecture represent the different Agents, EDR and SIEM available in M&NTIS. Keep in mind that Logstash is actually always enabled in any running simulation.
How to use
The Run Configuration is the page accessible before running an Unit Attack or a Scenario. You can access this page by clicking the button
Then, you land on the page with every EDR, Log Agents and Log Collectors or SIEM available in M&NTIS.
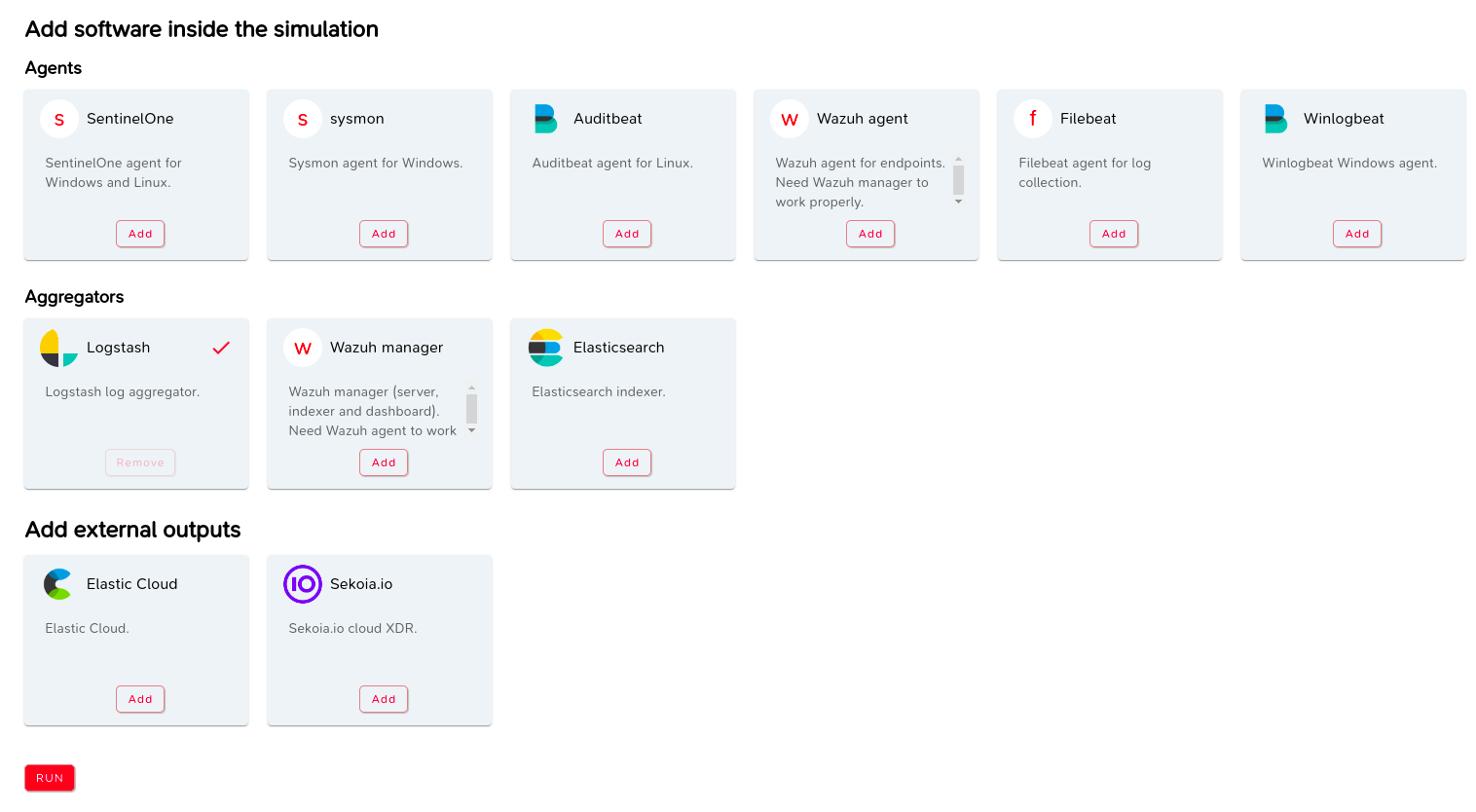
Most components have a default configuration. However, some of them require additional keys or tokens.
Warning
Not all component are compatible with each other. The documentation will provide guidelines to best configure your lab run.
Once the run is configured, you can click the Run button to start the simulation:
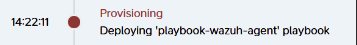
Finally, you need to wait for the provision of the corresponding component before using it. For example, if you configured your run to use Wazuh, wait for the step Deploying-wazuh-agent to finish as in the picture: