Cyber Training and Testing Platform for Defenders
Strengthen your SOC and CERT with M&NTIS. Hands-on defensive labs, live training, and nonstop testing to elevate your defenses.
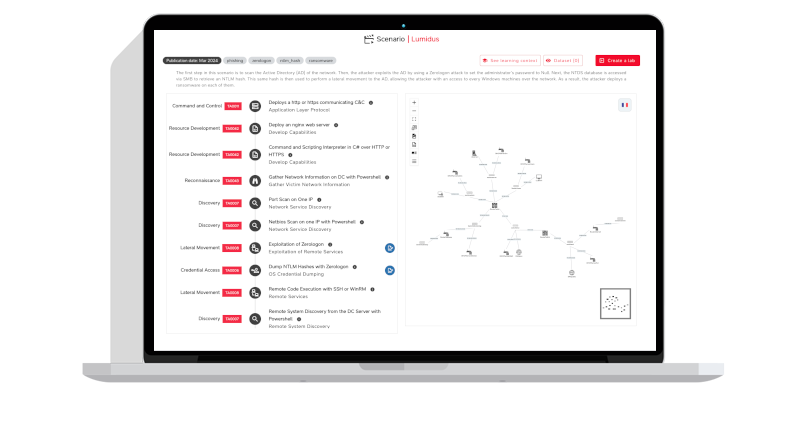
The All-in-One Platform for Blue Team Training and Continuous Defense Testing
M&NTIS Platform is a fully integrated SaaS environment designed to help SOC and CERT teams achieve validated defensive readiness through immersive, full-scale simulated environments, realistic live attack simulations, and continuous validation of detection and response workflows.
Immersive Environments
Full-scale simulated enterprise infrastructure with realistic endpoints, servers, AD, logs, EDR, SIEM, and legitimate activity.
Live Attack Simulations
Realistic adversary emulation executing full attack chains based on real-world techniques and intrusion sets.
Continuous Validation
Ongoing testing and validation of detection and response workflows, rules, processes, and tools.
Built for modern security operations, M&NTIS unifies training, testing, and performance assessment in a single, scalable platform.
Next-Level Blue Team Training & Defense Testing
Blue Team Training
Immersive training in a full simulated enterprise environment
Face live attack scenarios: Challenge your detection and response capabilities
Full-scale simulated IT environment: Endpoints, servers, AD, logs, EDR, SIEM, and realistic legitimate activity
Train with Your Stack: Use your everyday security tools (SIEM, EDR, ...)
Flexible Learning: Train in Solo or Team Mode
Defense Testing
Continuous validation of your rules, processes & tools
Run unitary attacks or full kill-chain scenarios to test your detections, measure visibility, and uncover blind spots
Schedule automated attack campaigns
Measure rule & detection coverage
Evaluate how your SOC reacts, how your tools perform, and how your processes hold up under real threat conditions
Built for Modern Security Teams
Organizations We Serve
Internal SOC & CERT units
Organizations building in-house defensive capabilities
MSSPs
Delivering advanced detection services to clients
Cyber training centers
Scaling Blue Team capabilities and certifications
Who Uses M&NTIS
SOC analysts
Detection engineers
DFIR / forensic specialists
Threat hunters
From hands-on training to continuous defense testing, M&NTIS powers the entire defensive workflow.
Advanced Defense Technology
Immersive Defensive Labs
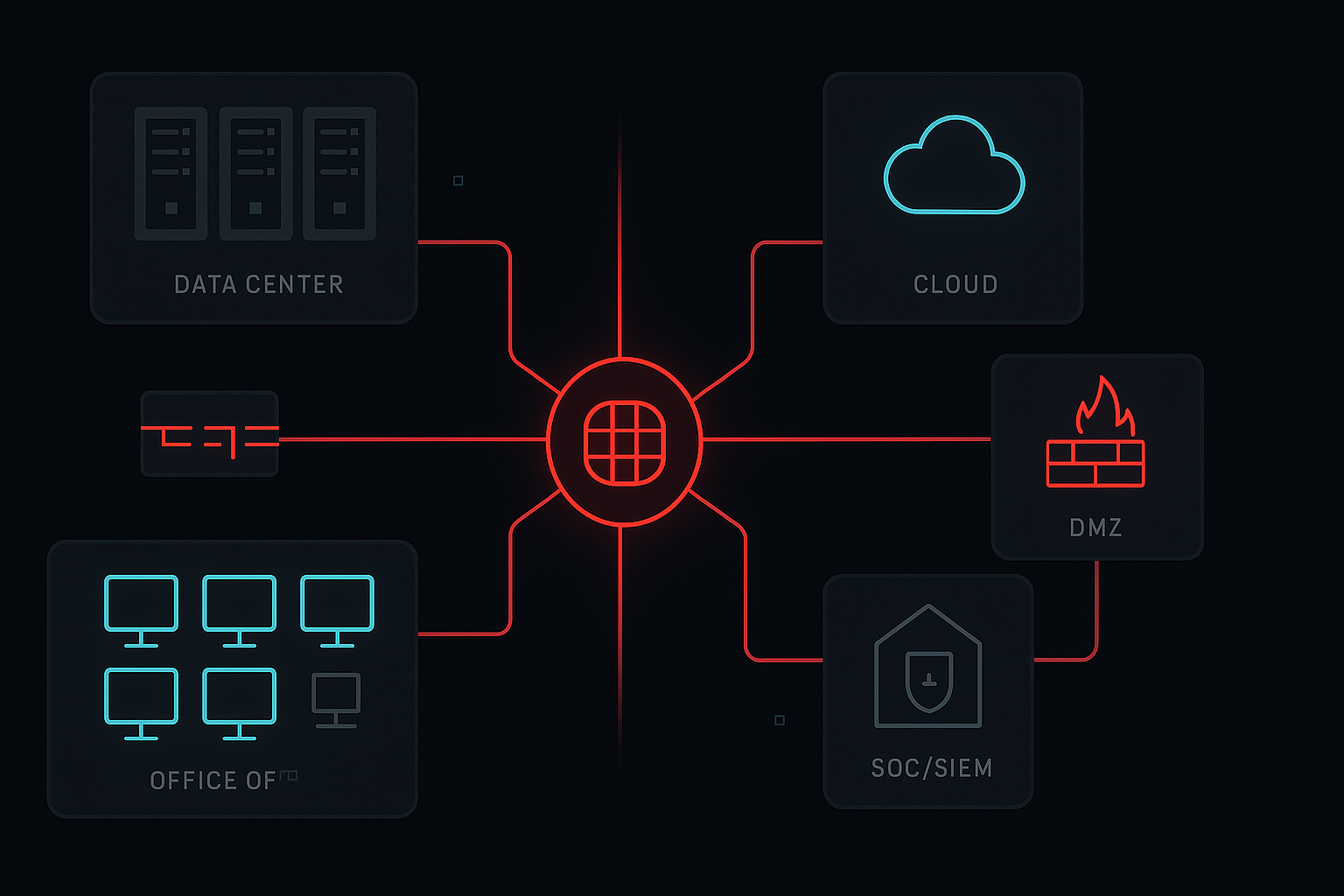
M&NTIS leverages a Cyber Range stack to recreate a full-scale enterprise IT environment.
Full-scale enterprise SI simulation with real assets and business activity
Hands-on, interactive environment for investigations and exercises
Replayable scenarios for continuous learning, skill-building, and testing

Real-Time Attack Simulations
Leveraging adversary emulation, M&NTIS executes full attack chains based on real-world techniques and intrusion sets.
Ransomware
Exfiltration of sensitive documents
Spyware on a fleet of machines
Sabotage of an IT network (wiping)
Supply Chain attack
M&NTIS allows attack steps to be launched on demand or automatically, adapting difficulty and scope to your team's skill level.
Seamless Security Stack Integration
Connect M&NTIS directly to your day-to-day SIEM or SOC tooling:
EDR and agents:
SentinelOne, Harfanglab, Azure Arc, Wazuh, Winlogbeat/Auditbeat, Sysmon, …
SIEM:
Microsoft Sentinel, Sekoia.IO, Elastic stack, Splunk, Graylog, …
Training and testing can leverage either in-lab SIEMs, ensuring full training isolation, or interconnect with your cloud-based SIEM (production or testing tenant), using your rules and your workflows, ensuring maximum operational relevance.
Legitimate Activity Simulation
M&NTIS models normal business activity to reflect real operational noise, so that attack actions occur within the flow of legitimate activity.
Analysts train to:
Differentiate signal from noise
Avoid false positives
Detect subtle indicators of compromise
Prioritize alerts effectively
This creates a learning environment that is far closer to reality than traditional lab setups.
Challenge your Team against our Advanced Scenarios
Click on a card to discover more details about each scenario.
Platform Benefits
-
Prepare Analysts for Real ThreatsHands-on training with realistic, updated scenarios.
-
Scale Training Across Teams and LocationsFully SaaS, no infrastructure required.
-
Validate Your Entire Defense StackFrom SIEM rules to response workflows and product effectiveness.
-
Reduce Security Blind SpotsContinuous testing exposes gaps before attackers do.
-
Improve SOC & CERT EfficiencyBetter investigations, fewer mistakes, faster responses.
Ready to Elevate Your Defense?
Join leading security teams using M&NTIS to build validated defensive readiness.






