Sentinel One
Sentinel One
Description
The EDR SentinelOne can be deployed within some Virtual Machines of the simulation.
Its agent is available on both Linux Ubuntu and Windows 10/Server 2016. Sentinel One's alerts and logs have to be sent to a Management Console compatible only.
This agent works by using a token. This token helps the agent to retrieve its configuration online against the Management Console.
Then, the direction is from the agent to the Cloud only.
Configuration
Currently, Sentinel One within M&NTIS is configured to only log the incident. It does not try to stop an attack.
Sentinel One requires a Management Console in order to work, which you have to get on your own since it is not provided by M&NTIS.
How to enable
You need to provide the Site or Group token. You can retrieve it by logging in the Management Console, selecting your site or group, and then click on the "Site Info" or "Group Info" tab. Copy the provided token.
On the M&NTIS' run configuration page, click on "Add" within the Sentinel One's box, and paste the token.
Usage
Log in your Management Console. Then, select the appropriate site and/or group where your token is generated.
In our example, the site is majj-nfr2 and the group is mantis.
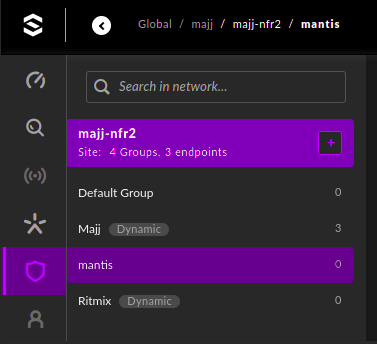
To assess if the agent has successfully contacted the Management Console, go to the Sentinels icon:

Your agent(s) should appear. Then, to check for alerts sent from the agents, you can click on the Incidents icon:

