Scenario overview
A threat actor exploits a public-facing vulnerability on a Linux server and poisons network communications to the DMZ WSUS server. The attacker is then able to carry out a supply chain attack by deploying a malicious Windows update. A stealthy way to compromise all the machines!
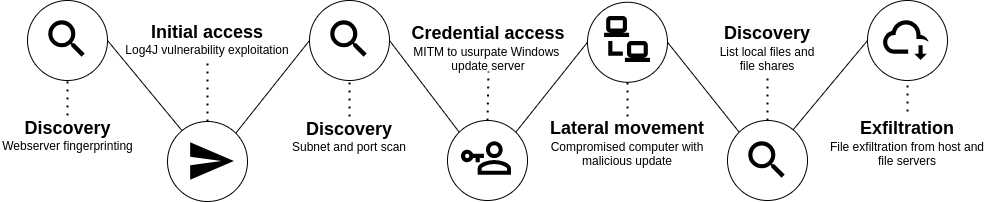
A threat actor exploits a public-facing vulnerability on a Linux server and poisons network communications to the DMZ WSUS server. The attacker is then able to carry out a supply chain attack by deploying a malicious Windows update. A stealthy way to compromise all the machines!


