Scenario overview
An attacker wants to steal the company’s R&D secrets. They exploit a vulnerability in a public-facing Linux server to gain access to the company’s network. Using an AITM attack, the attacker succeeds in stealing sensitive information. The R&D secrets may interest competitors!
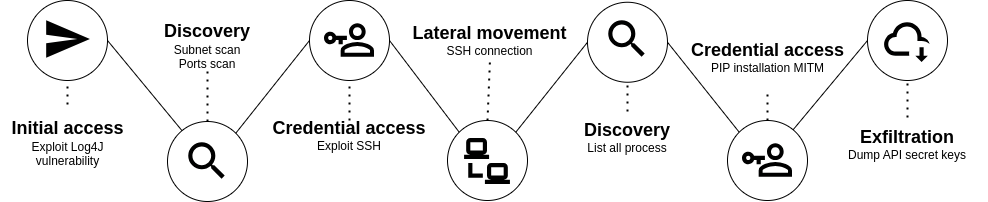
An attacker wants to steal the company’s R&D secrets. They exploit a vulnerability in a public-facing Linux server to gain access to the company’s network. Using an AITM attack, the attacker succeeds in stealing sensitive information. The R&D secrets may interest competitors!


