Scenario overview
A threat actor is going to ransom an entire company infrastructure. They first compromise a user workstation via phishing, then exploit the Zerologon vulnerability to get a privileged access to the domain controller. A good place to launch the final stage!
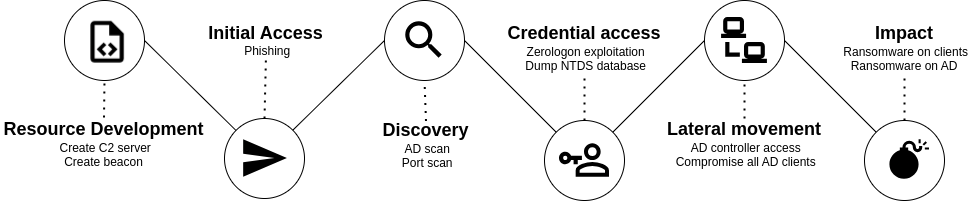
A threat actor is going to ransom an entire company infrastructure. They first compromise a user workstation via phishing, then exploit the Zerologon vulnerability to get a privileged access to the domain controller. A good place to launch the final stage!


