Scenario overview
A threat actor wants to destroy all company data. They first compromise a user workstation via phishing, then escalate their privileges to dump domain admin credentials from memory. The domain controller is not safe anymore!
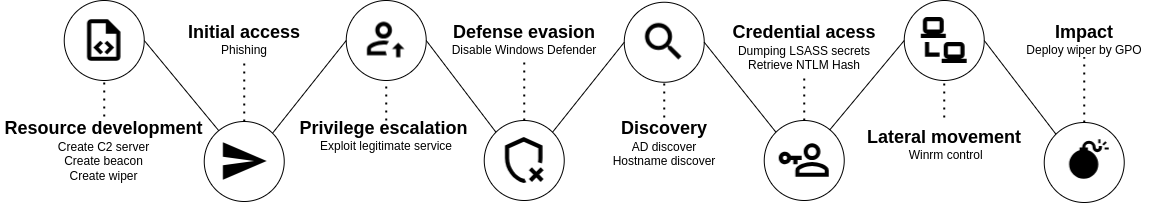
A threat actor wants to destroy all company data. They first compromise a user workstation via phishing, then escalate their privileges to dump domain admin credentials from memory. The domain controller is not safe anymore!


