Scenario overview
An attacker seeks to steal confidential company data. After a successful phishing attempt, they carry out a MITM attack and succeed in breaching an admin workstation. A good place to “legitimately” access and exfiltrate sensitive files!
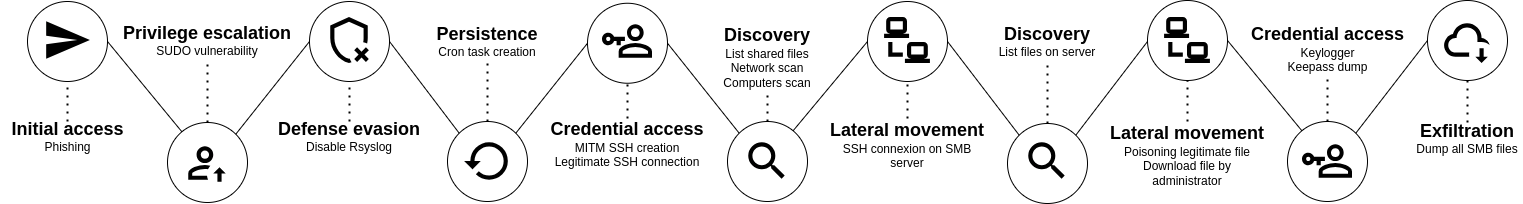
An attacker seeks to steal confidential company data. After a successful phishing attempt, they carry out a MITM attack and succeed in breaching an admin workstation. A good place to “legitimately” access and exfiltrate sensitive files!


