Scenario overview
An attacker responds to a job offer with a malicious attachment. Thanks to this initial compromise, he spreads across the company's various file shares. Eventually, he compromises an administrator and steals all the company's data. This realistic scenario allows to emulate TTPs from the Dark Pink intrusion set.
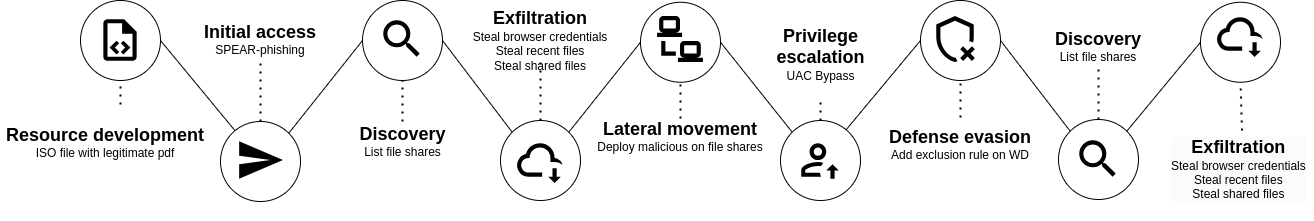
An attacker responds to a job offer with a malicious attachment. Thanks to this initial compromise, he spreads across the company's various file shares. Eventually, he compromises an administrator and steals all the company's data. This realistic scenario allows to emulate TTPs from the Dark Pink intrusion set.


