Microsoft Azure Arc Agent
Microsoft Azure Arc Agent
Description
Azure Cloud is the Microsoft's SIEM for log gathering and analysis where the Azure Monitor Agent sends its logs.
Glossary
- Azure Monitor Agent (AMA): it is responsible for monitoring and collecting data from running machines. It then delivers the data to Microsoft service (such as Azure Sentinel, Azure Cloud, and so on).
- Azure Arc: it lets you manage Windows and Linux physical servers and virtual machines hosted outside of Azure, on your corporate network, or other cloud provider. It works as a bridge to Azure.
- Azure Sentinel: it is a cloud native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution that runs in the Azure cloud.
- Azure Log Analytics Workspace: it is a data store where you can collect any type of log data from all of your Azure and non-Azure resources and applications.
- Data Collection Rule (DCR): it is a part of an Event Trace Log (ETL)-like data collection process which improves on legacy data collection methods for Azure Monitor.
Configuration
The M&NTIS implementation is compatible with Microsoft's Azure CLI (Command Line Interface). Each machine where Azure Arc Agent is installed from this lab has a tag creator=mantis. The Windows and Linux machines of the simulation are provisioned with the Azure Arc Agent and the Azure Monitor Agent extension enabled. The extension is configured to send logs via a proxy embedded in the lab. Azure has to be configured from the Cloud side and not from the agent.
Note the resource_group you will use and where all the dynamic objects will be created. The geographic location is a mandatory field by Azure. For the example, "francecentral" can be used.
Application registration
It is expected that an application is created in order to impersonate the main user. To achieve this, go to "App Registrations" -> "New registration". Configure the web redirection URL with "http://localhost" (it won't be used). Validate this app creation and then go to this newly created app. Please note the client_id and Directory ID, known as tenant_id. Then, click on Manage -> Authentication -> Advanced settings. Enable the "Allow public client flows" option. To create a new secret, navigate to Manage -> Certificates and Secrets. Create a new client secret and note this value as client_secret.
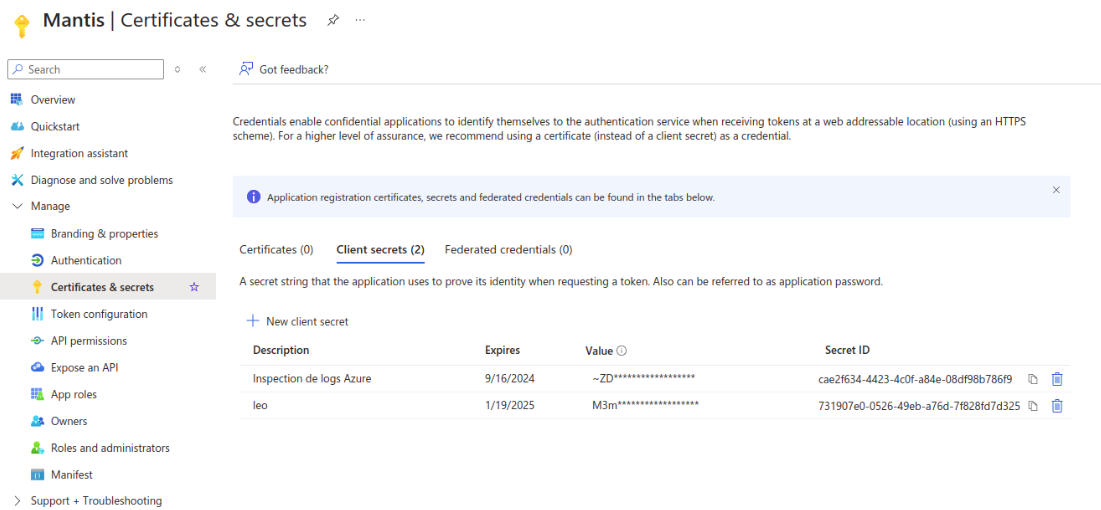
In Manage -> API Permission, create a new permission for the Azure Service Management, and choose a delegated permission and check the user_impersonation entry.
Now, navigate to Manage -> App roles, and add both roles:
- Microsoft.Resources/deployments/validate/action
- Microsoft.HybridCompute/machines/extensions/write
Role assigments
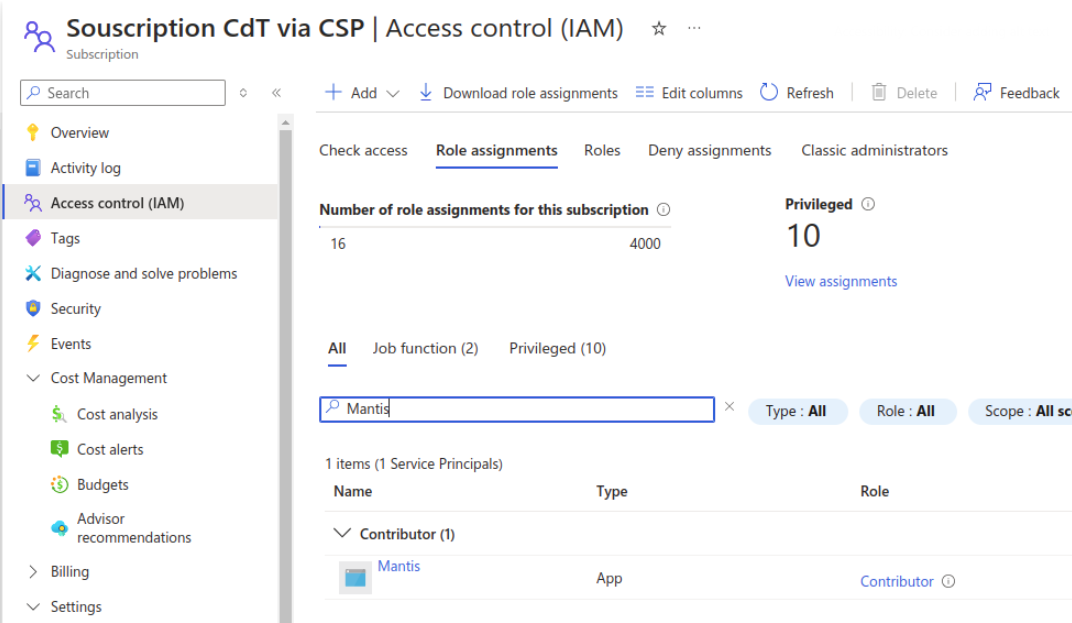
You need to grant the Contributor role for the app for both the subcription and the target resource group.
Subscription
You need to allow this registered app to your subscription plan (subscription_id). To achieve this, you need to go to the subscription's page. Then, navigate to Access Control (IAM), add your app, and set its role to contributor.
Resource group
The exact same operation has to be performed on the resource group. Navigate to the Access Control (IAM) tab on the left pane, and add your app as a contributor.
Data Collection Rule (DCR)
Basic configuration
Now it's time to create a Data Collection Rule DCR. This is where logs from the various machines will be sent and parsed by the Data connectors. At runtime, M&NTIS automatically adds machines to the corresponding DCR. These machines are then visible in the resources tab. You have to create 3 different DCRs. All of them are optional. There 2 created from the data connectors and 1 extra not connected to a Data Connector. The user has to enable 2 Data connectors from the Azure Sentinel pane and create a specific DCR on each:
- Windows Security Events via AMA
- Syslog via AMA
and an extra general DCR for Windows Event Logs.
You have to remember the different DCR names as they are used in the configuration of the M&NTIS Azure Arc connector.
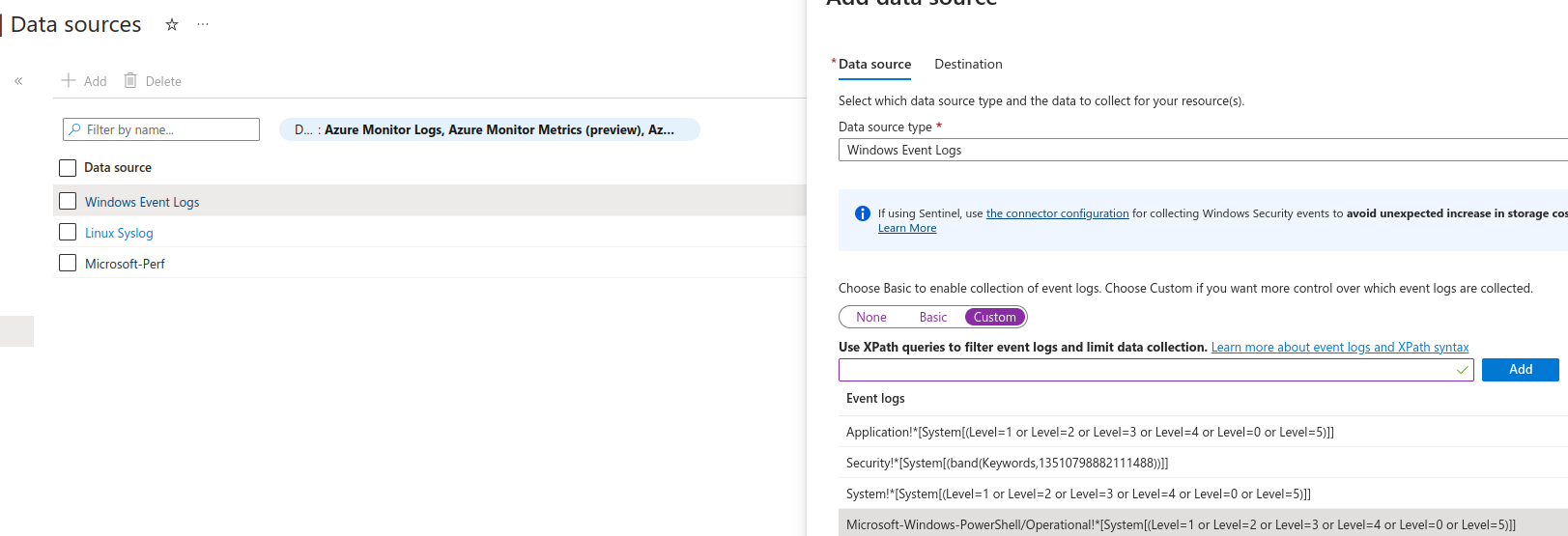
Powershell-transcript
Windows machines in the lab have the Powershell Transcript feature enabled. It allows to log as Event every Powershell command or Powershell script executed. Such events are registered in the Microsoft-Windows-PowerShell/Operational log file. In order to allow Azure to collect these events, you need to add the next rule as a "custom" XPath query in the Windows Event Logs:
Microsoft-Windows-PowerShell/Operational!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]
Log Analystics Workspace
In order to analyze all these logs, we need to create a Log Analytics workspace object. Add the newly created DCR to the Settings -> Agents -> Data Collection Rules tab.
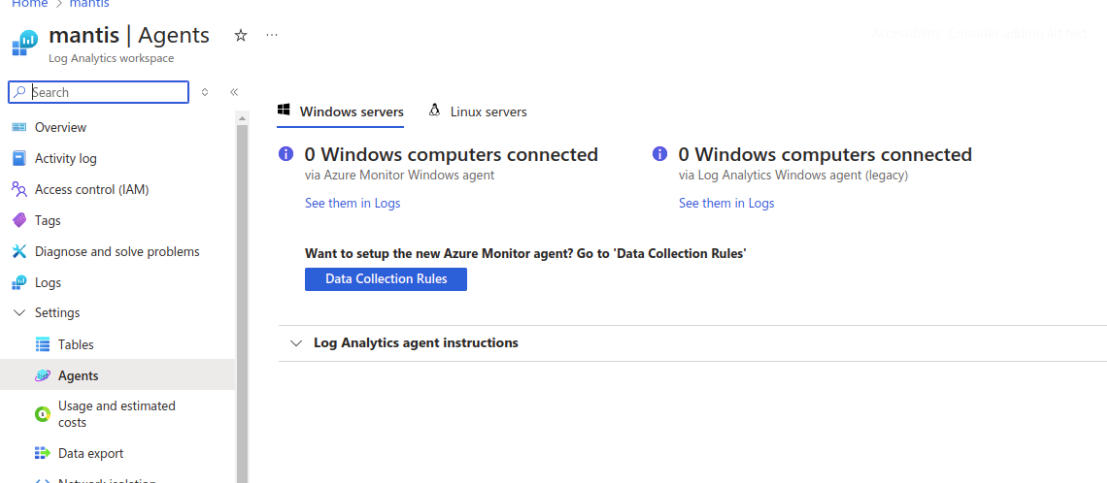
Now, navigate to Access Control (IAM), and add the Builtin role:
- Azure Connected Machine Onboarding.
Then, add the following permissions (which can be gathered in a custom role):
- Microsoft.HybridCompute/machines/delete
- Microsoft.Resources/deployments/*
- Microsoft.Resources/deployments/validate/action
- Microsoft.HybridCompute/machines/extensions/write
- Microsoft.Insights/DataCollectionRuleAssociations/Read
- Microsoft.Insights/DataCollectionRuleAssociations/Write
- Microsoft.Resources/subscriptions/resourcegroups/read
- Microsoft.Insights/dataCollectionRules/read
Security alerts retrieval
To retrieve security alerts generated by Microsoft Sentinel following log analysis, the M&NTIS Platform must be granted permission to perform KQL (Kusto Query Language) queries on the target workspace. Therefore, the Workspace ID must be provided if the user wants to correlate attacks with triggered alerts. The workspace_id field is optional. If it is not filled in, M&NTIS will not retrieve any security alerts from Microsoft Sentinel.
For M&NTIS to execute KQL queries on the SecurityAlert table of the target workspace, specific permissions must be granted for the application on the Log Analytics workspace.
- Service Principal to assign permissions to: (specify the service principal created above, i.e. the registered application)
- Role to assign: Log Analytics Reader
How to enable Azure Arc in M&NTIS
In order to use the M&NTIS connector for Azure, the user has 8 different Azure resources to configure. Such resources provide identifiers and tokens which are explained in Configuration
Usage
You can directly go to the main page of the Log Analysis Workspace you created earlier, and select Logs. You should see the logs sent from all the machines where AMA is installed in the lab. Depending on your plan, you can even use Azure Sentinel in order to detect threats.

