Attacks
Introduction
This page shows the attacks implemented within M&NTIS Platform. By default, these attacks are presented in the MITRE ATT&CK view.
The MITRE ATT&CK matrix
The MITRE ATT&CK matrix (Adversarial Tactics, Techniques, and Common Knowledge) is a matrix that lists the tactics and techniques used by cyber attackers.
This matrix is used to model and list existing threats, in order to improve defence strategies in response to these threats.
Threats are classified and prioritised in the form of TTPs (Tactics, Techniques, Procedures).
Each attack available within M&NTIS Platform represents the implementation of a technique or sub-technique of the MITRE ATT&CK, each technique or sub-technique belonging to a given tactic.
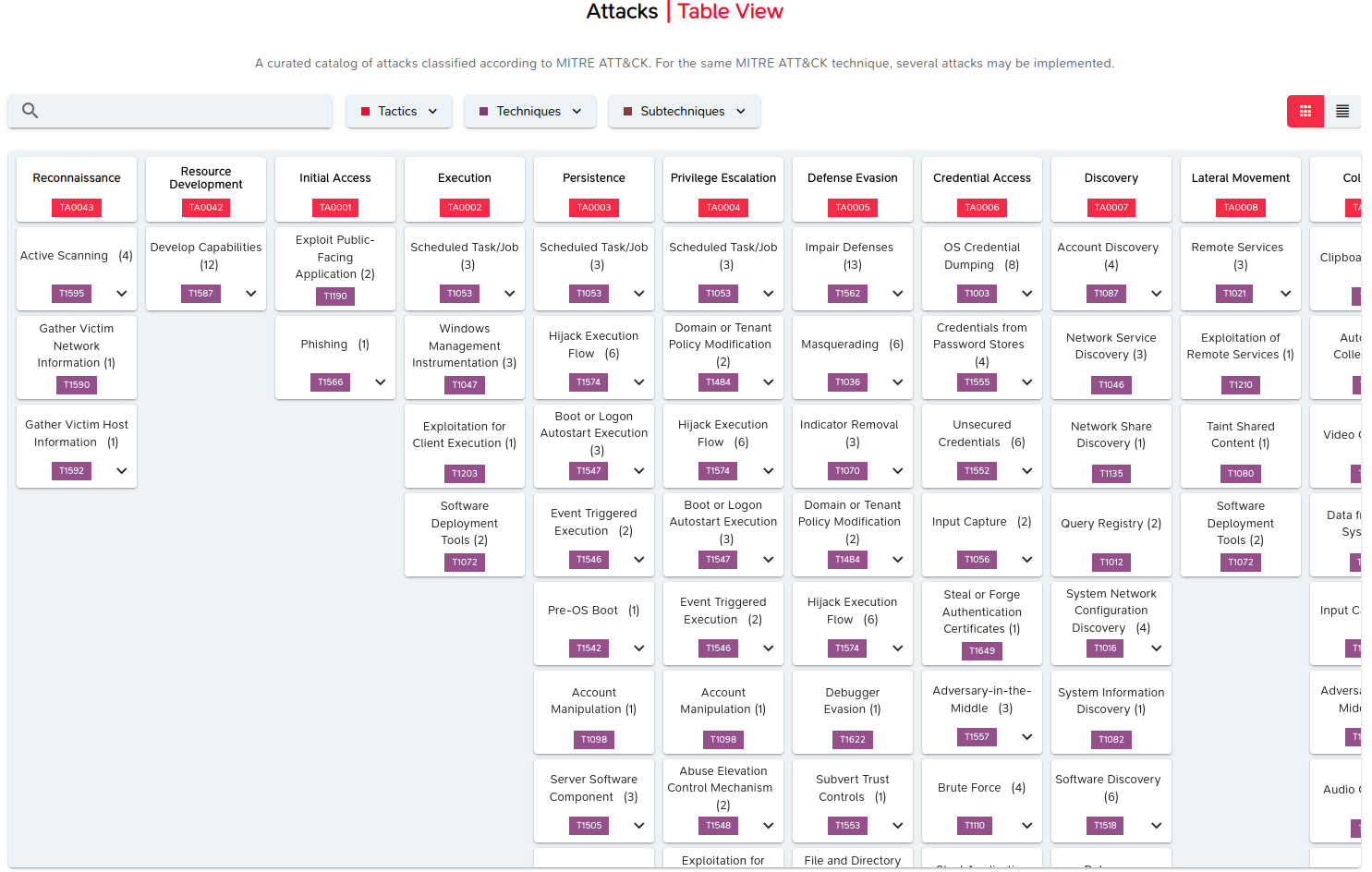
The MITRE ATT&CK view within M&NTIS Platform
The view resumes the matrix presentation, i.e. the tactics are presented in columns and in the same order, with the ID of each tactic displayed (for example TA0043 for the "Reconnaissance" tactic).
If all the columns (the tactics) are not visible, you can use the horizontal scroll bar.
Similarly, the techniques for each tactic are presented online, and if some are not visible, you can use the vertical scroll bar.
For a given tactic, only the techniques for which there is at least one implementation (an attack) are shown. For example, the "Initial Access" tactic includes a total of 10 techniques, but hereafter only two techniques are implemented via attacks within M&NTIS Platform.
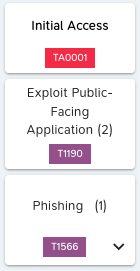
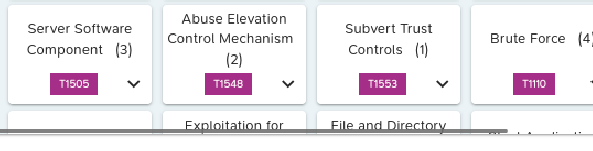
Each "box" representing a technique contains the following information:
- The name of the technique (e.g. ‘Phishing’),
- The ID of the technique (for example ``T1566‘’),
- The number of attacks implemented for this technique (in brackets, e.g. 2 for "Exploit Public Facing Application").
Note that if there is a "down arrow" in the box (e.g. for "Phishing"), clicking on it displays the names of the sub-techniques of the technique concerned and, in brackets, the number of attacks implementing this or these sub-technique(s):
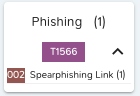
Clicking on the "up arrow" hides this information.
Clicking somewhere else in the box displays the list of attacks implemented for the technique in question.
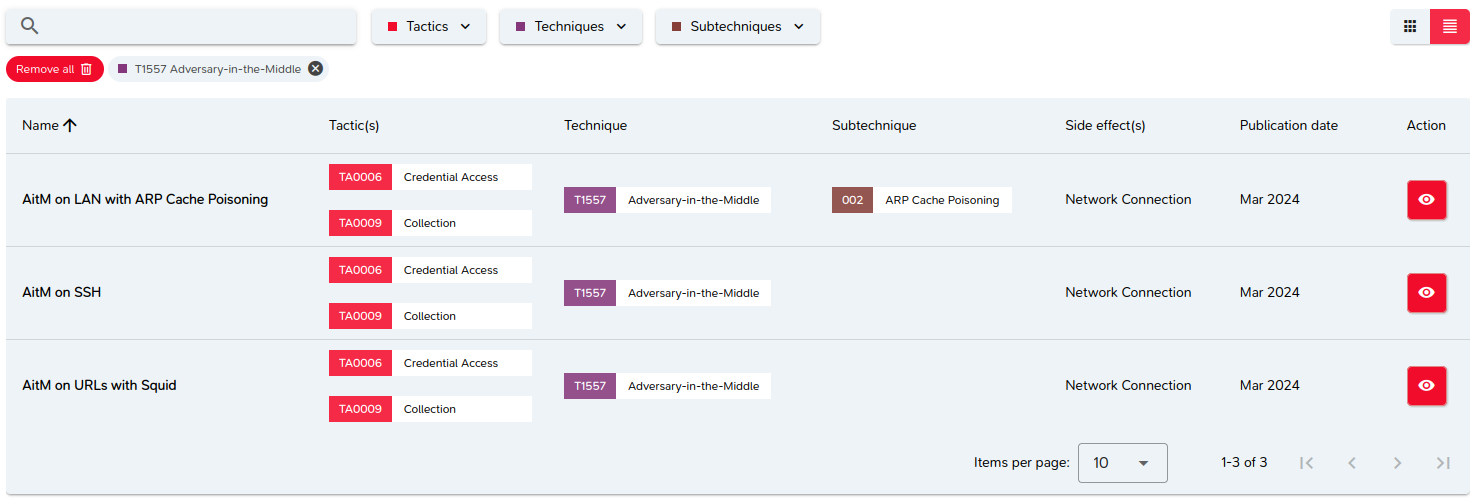
Viewing attacks as a list
Attacks can also be viewed in the form of a paginated list, where attacks are sorted alphabetically by name.
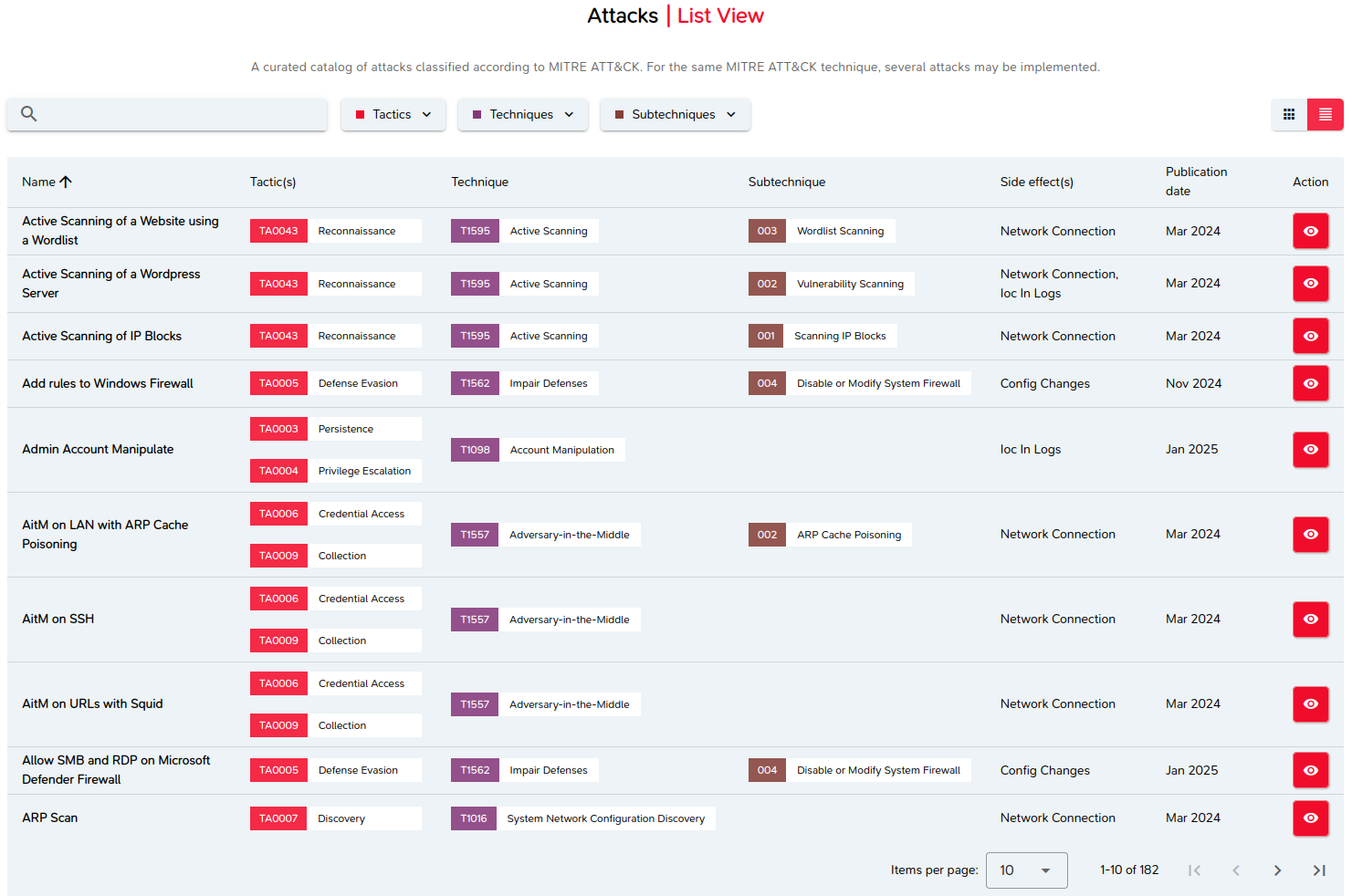
Attacks implemented by technique
This view lists the different attacks available for a given technique.
It is equivalent to applying a filter bearing the ID and name of the technique in question.